By Regine Bonneau, CEO - RB Advisory LLC

Governmental entities – Cyber Threat landscape and the Presidential Executive Orders
Local and State officials are tasked with protecting the confidentiality, integrity, and availability of sensitive data, networks and systems. Governmental entities need to understand cybersecurity and how it affects them.
Local governments must monitor the growing emerging threat landscape. This is not possible without the proper tools, government backing, budgets, compliance mandates and a team of skilled information security practitioners. Government backing and budget increase will help with the initiatives set forth by the 2 Presidential Executive Orders of February 2013 and May 2017, and NIST.
The Presidential Executive Orders on Cybersecurity and NIST
According to Section 1(a)(b)(c) of the Presidential Executive Order of May 11, 2017, heads of all agency will be held accountable for managing cybersecurity risk by maintaining awareness of cyber threats. They must detect anomalies and incidents that are affecting IT and data. Most importantly each agency has to incorporate cyber risk management plans and submit their plans to the Department of Homeland Security (DHS).
Additionally Section 1(c)(ii)(A)(1)(2) (B) – Risk Management, requires a risk report to contain:
(A) a risk mitigation and acceptance choices made by each agency with:
1. the strategic, operation, and budgetary considerations that informed those choices; and
2. any accepted risk, including from unmitigated vulnerabilities; and
(B) describe the agency’s action to implement the Framework.
The Presidential Executive Order Of February 12, 2013 provides a detail explanation of improving critical cybersecurity infrastructure. Special attention to Section 7 – Baseline Framework to reduce cyber risk to critical infrastructure with elaboration to the Cybersecurity Framework, which shall include:
a) A set of standards, methodologies, procedures, and processes that align policy, business, and technology to tackle cyber risk
(b) A prioritized, flexible, repeatable, performance-based, and cost-effective approach for information security measures and control that will help in identifying, assessing, and managing cyber risk
Section 10 – Adoption of Framework, which focuses on:
(a) Agencies engagement with consulting process with Department of Homeland Security (DHS), Office of Management and Budget (OMB), and National Security Staff for reviewing the Cybersecurity framework
The National Institutes of Standards and Technology (NIST) have provided a Cybersecurity Framework (CSF) to help government entities select security and privacy controls to protect operations, assets, and individuals from cyber attacks. When the controls are implemented, they help manage information security and privacy risk. The NIST Cybersecurity Framework helps Governmental entities meet the security and privacy requirements expressed in the Presidential Executive Orders of February 2013 and May 2017.
NIST Cybersecurity Framework section to pay attention to:
♦ Technology and policy neutrality security controls encourage organizations:
• To pay attention to security capabilities that align with the mission/business success and protection of information.
• Analyze each security control and how it is applicable to technology, environments of operation, missions/ business functions, and community interest.
• To specify security policies tailored to security controls.
♦ Privacy Controls:
• Best practices to help the organization align with federal laws, Executive Orders, directives, instructions, regulatory policies, standards, guidance and organization-specific issuance.
• Have a direct relationship between privacy and security controls.
• Demonstrate implementation, assessment, and ongoing monitoring of these controls.
• Most importantly, promote cooperation between privacy and security officials in order for key objectives to be met on time.
Why are the above important when talking to the Governmental entities? Let’s take a look at the challenges faced by the Governmental entities below.
Governmental entities challenges and guidance:
Alarming facts to consider and not in favor of Governmental entities:
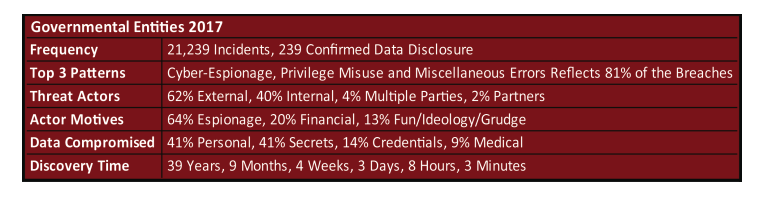
♦ Governmental entities have the following challenges:
• They are required to report up the chain on incidents that have occurred within their organization that may not have been considered or detected.
• Governmental entities are large in size.
These two indicators place governmental entities in great danger and exposure to massive cyber incidents.
Local governments have an enormous and ever emerging set of information assets and operations with distinctive levels of risk and vulnerability. From initial risk assessment to emergency backups and recovery, the cybersecurity team of governmental entities has a huge job that is only getting bigger as new data are being collected, stored, and accessed on a daily basis.
♦ Governmental entities need to focus and invest in:
• Assessment of IT Risk, including governance and application – First crucial steps to properly allocate the correct solution that will provide the greatest protection and ROI.
• Secure credit card processing systems.
• Secure networks and systems.
• Technical security training – improve your teams ability to fight against external and internal threats. Continuous training and engagement with other team members, industries leaders, and private companies will have a major impact.
• Data flow mapping – Know where the data is resting to make it more efficient.
• Process improvement projects to maximize efficiency.
• Identity governance and access management – this is key and helps prevent a lot of breaches of personal identifiable information by employees.
• Education and Awareness Training – not only helps employees and staff recognized known threats and report them; it builds employee morale and reinforces ethical behaviors. It is a key indicator in the crusade of fighting Insider Threats.
• Let’s not forget the multiple cloud environment that needs to be properly managed and secured.
♦ In order to start minimizing these incidents and start remediation on a timely manner, a governmental entity needs to consider the following:
• Know your data and where it is located.
• Know who has access, and who does access it.
• Set up controls to monitor data ingress and egress.
• From national security to local zoning boards, every agency needs to know and understand the threat factors to their department and also how it affects the other departments.
Governmental entities depend on complex sets of networks and communication that are part of the National critical infrastructure, which needs to be secured. A great amount of effort and initiatives are needed to help secure this critical infrastructure because the information and data they hold is key to the Nation’s security and survival.
Resources:
Regine Bonneau is a leading expert on cyber security, risk management and compliance. Her career spans 20 years with a focus on technology and processes in the healthcare, financial and energy sectors. Ms. Bonneau is the Founder/CEO of RB Advisory LLC, which provides cyber risk management, security assessments, compliance services, forensic audits and privacy consultations for private sector and government clients. She is a sought after speaker and holds leadership roles in several technology industry associations. Ms. Bonneau has been featured in the Orlando Sentinel, the Orlando Business Journal and other prominent publications. Regine’s areas of expertise are Risk Management, Cyber Risk Management, Compliance, cybersecurity, systems and technology, product development, anti-money laundering (AML), risk and controls, Education and training.
Regine Bonneau - Office: 407.796.8079 Cell: 954.330.6015 Email: [email protected] Website: www.rbadvisoryllc.com
